The information age has changed the way we handle our banking and manage our finances. What we must not forget is that this includes how criminals operate, the vast majority are turning to technology to strengthen their approach. A lack of action could result in a data breach which, on average, has a total cost of 4.2 million euros. Your bank needs to be prepared, and there are several ways to determine whether your bank or financial institution is secure or not. One of them is penetration testing, and that is exactly what we are going to elaborate on in this blog.
Do you know what is going on in this sector regarding email security and secure communication? And perhaps more importantly: does your organization currently have the right security to prevent a data breach? Take a look here: Secure emailing in the financial sector
What is penetration testing?
A penetration test, or simply known as a pen test, is a simulated cyberattack against your computer or security system to check for potential vulnerabilities before they can be exploited by hackers. Insights provided by a pen test can be used to fine-tune your IT policies and patch any detected gaps in security.
In general, there are two categories of penetration testing that tend to apply to financial institutions. These are customer-focused or compliance-driven, versus penetration tests that attempt to exploit people, process, or technology with the objective of breaking into the network and gaining access to sensitive data.
1. Box Testing to identify gaps in security.
These are main types in banking.
-
Black Box Testing
Black box testing focuses on a lack of information, employing the tools and techniques a hacker would use to penetrate security. This type of test is also known as a blind test or real-world hacking simulation test.
-
White Box Testing
In this case, the penetration tester has full access to information about the organization’s network infrastructure or applications to be tested, including network diagrams and protocols, the IP address schema, source code, etc. This type of test is also known as clear box testing or glass box testing.
-
Gray Box Testing
Lastly, the penetration tester is given partial knowledge of the internal network or web application. The main advantage of this type of test allows the tester to focus initial efforts on identifying the areas that present the most significant security risks to the business. This type of test combines both white box and black box testing techniques with a more efficient focus and approach.
2. Pen tests attempting to exploit people, process or technology with the aim of forcing access to sensitive data.
The second scenario describes a more traditional pen test. It covers exploitation attempts against People, Process, and Technology.
This type of pen test is a simulation that involves two teams on opposite ends. The hackers are known as team Red, defense as team Blue. This is a far more realistic way to test the security readiness and responsiveness of an organization as it emulates a real-life situation.
Advantages of doing a pentest:
1. Reveals vulnerabilities
As mentioned before, a pen test explores existing weaknesses in your system by scanning application configurations and the network infrastructure. This is quite a deep scan since even actions and habits of your staff that could lead to data leaks and malicious infiltration are being researched during testing.
To conclude, a report informs you on your vulnerable points, so you know exactly what software and hardware improvements you must consider or what recommendations and policies would improve your overall security.
2. Show real risks
Once these points of weakness are found, penetration testers then try to exploit them. This allows businesses insight into what an attacker could do in the ‘real world.’ Realistically, they might attempt to access sensitive data and execute operating system commands.
It is important to consider that testers might also tell you that a vulnerability that is theoretically high-risk is not necessarily that risky at all due to how hard it can be to exploit. Only a specialist can perform that type of analysis, which is why many organizations choose to outsource their penetration testing.
3. Test your cyber-defense capability and responsiveness.
In the event of a cyber-attack, your defense should be able to detect attacks and respond adequately and on time. Once you detect an intrusion, you should start investigating, look for the intruders and block them. Whether they are hackers, or experts testing the effectiveness of your protection strategy.
4. Ensure business continuity.
To keep your business operations running, you need network availability, 24/7 communication, and access to resources. Any disruption has a negative impact on your organization. Pentests help ensure that your operations don't suffer from unexpected downtime or loss of accessibility. In this respect, a pen test is similar to a business continuity audit.
5. Get an informed opinion from a third party.
When someone internally identifies a problem, your management may not be inclined to respond immediately. A report from an external expert often has a greater impact on your management and is more likely to elicit a response.
6. Follow regulations and certifications.
Your industry and legal compliance requirements may prescribe a certain level of pentesting. Consider the ISO 27001 standard of PCI regulations, which requires all managers and system owners to conduct regular pen tests and security checks with competent testers. That's because pen testing focuses on real-life consequences.
7. Be confident.
A data breach cyber-attack negatively impacts the trust and loyalty of your customers, suppliers and partners. However, if your organization is known for its rigorous and systematic security assessments and pen tests, reassure all those interested.
The 7 Steps of Pentesting
According to KirkPatrickPrice’s methodology, there are 7 stages of penetration testing. However, it is important to note that these may differ from what you might have seen before. Different methods of pentesting around the world tend to have slight variations in the process, but the main stages remain the same for the most part.
This is a general model of the pen test process:
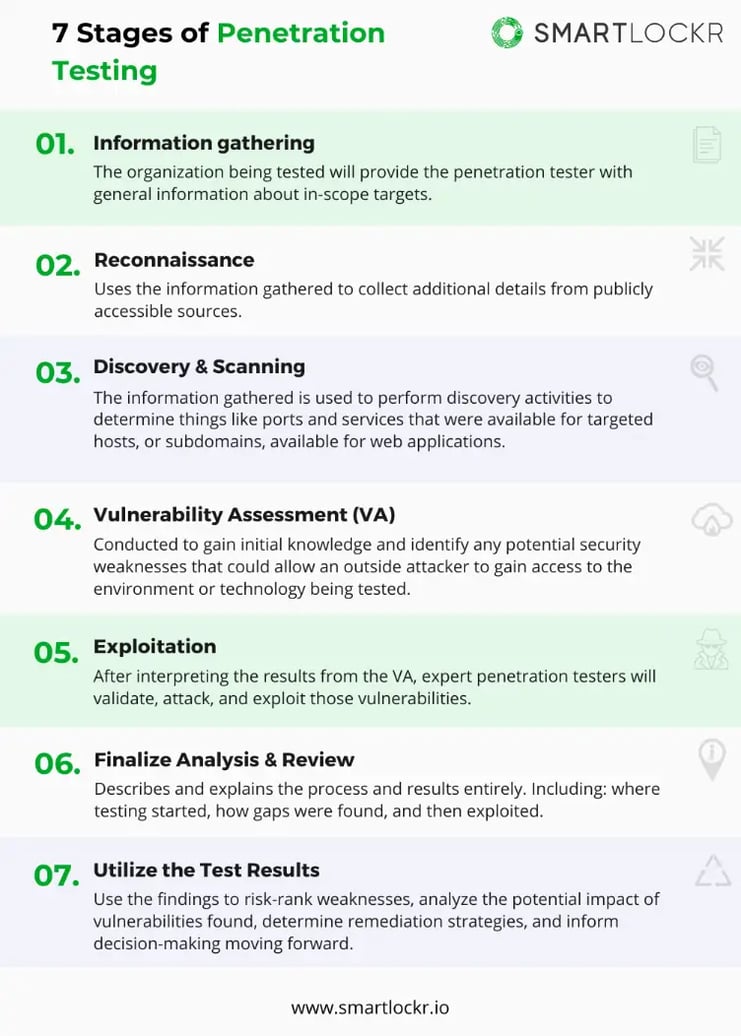
- Information gathering: The organization being tested will provide the penetration tester with general information about in-scope targets.
- Reconnaissance: Uses the information gathered to collect additional details from publicly accessible sources.
- Discovery and scanning: The information gathered is used to perform discovery activities to determine things like ports and services that were available for targeted hosts, or subdomains, available for web applications.
- Vulnerability assessment (VA): Conducted to gain initial knowledge and identify any potential security weaknesses that could allow an outside attacker to gain access to the environment or technology being tested.
- Exploitation: After interpreting the results from the VA, expert penetration testers will validate, attack, and exploit those vulnerabilities.
- Finalize Analysis & Review: Describes and explains the process and results entirely. Including: where testing started, how gaps were found, and then exploited.
- Utilize the Test Results: Use the findings to risk-rank weaknesses, analyze the potential impact of vulnerabilities found, determine remediation strategies, and inform decision-making moving forward.
Don’t forget to exercise caution! If conducted badly, it can cause congestion and result in systems crashing. It is common for organizations to outsource pentesting to industry experts and specialists.
The importance of pentesting has only become more evident, especially in a digitalized world that requires you to swim, or you will sink. Pentests allow you to identify gaps in your organization’s security before criminals with malicious intent do and take advantage. Understanding your organization’s weakness enables will allow you to strengthen your defense before the damage can be done. So, whether your reason for implementing pentesting is motivated by security or compliance with laws. At the end of the day, prevention is always better than the cure.